Mobile Device Management (MDM) is a way for businesses to manage the devices that connect to their networks, including smartphones, tablets, laptops, and other devices. There are four main models for MDM: BYOD, CYOD, COPE, and COBO. Each model has its own advantages and disadvantages, and the right model for a business depends on its needs.
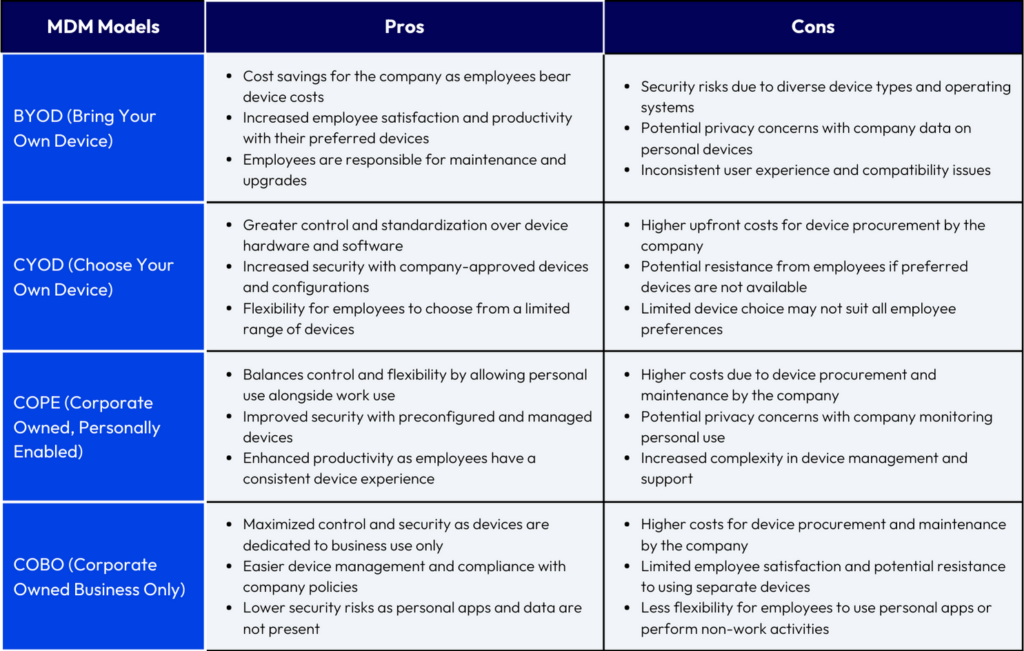
BYOD (Bring Your Own Device)
BYOD is the most popular MDM model. It allows employees to use their own personal devices for work purposes, which can provide advantages such as cost savings (as the company does not have to purchase devices for its employees) and increased employee satisfaction (as they are already familiar with their own devices and how to use them).
However, it also comes with some risks, as there is no way for the company to control or manage the devices, which can lead to security breaches and data leaks, as well as compatibility issues.
This can pose a challenge for IT departments, who must manage and secure these devices while maintaining employee privacy. Here is where MDM can help IT departments manage BYOD devices by providing a way to enforce security policies, distribute apps, and remotely wipe data if a device is lost or stolen.
CYOD (Choose Your Own Device)
CYOD, or choose your own device, is a model where the company provides a list of approved devices that employees can choose from. This gives the company more control over the devices that are being used, and can help to avoid compatibility and security issues.
The disadvantages of CYOD are that it can be more expensive for the company, it can be challenging to keep up with the latest devices and operating systems, and employees may be less engaged if they’re not using their own personal devices.
COPE (Corporate-Owned, Personally-Enabled)
COPE, or company-owned, personally-enabled, is a model where the company provides devices for employees to use, but employees are able to use them for personal reasons as well. The advantages of COPE are that it is easier to manage and secure devices, and employees are less likely to use their devices for personal reasons.
The disadvantages of COPE are that it can be more expensive for the company, and employees may be less satisfied with the devices they are given.
COBO (Corporate-Owned, Business-Only)
In the COBO model, the company provides employees with corporate-owned devices that can only be used for work purposes. This is the most secure model, as it helps to keep work and personal data separate, and ensures that the devices are only used for work-related activities.
However, it can be expensive to provide devices for every employee, and some employees may prefer to use their own devices.
Make a Decision Based on your Specific Needs
The right MDM model for you will depend on your specific needs. Here are some factors to consider:
- How many devices do you need to manage
- What types of devices do you need to manage
- What level of control do you need over the devices
- How much data do you need to collect and store
- How much security do you need?
- What is your budget
Once you’ve considered all of these factors, you can narrow down your options and make a decision. If you need to manage a large number of devices, you might want to consider a BYOD model. This will allow you to give employees more freedom when it comes to choosing their device, but it will also require more work on your part to manage and secure the devices.
If you need to manage a smaller number of devices, or you need more control over the devices, you might want to consider a CYOD or COPE model. These models will give you more control over the devices, but they will also be more expensive.
If you need to collect and store a lot of data, you might want to consider a COBO model. This will allow you to centrally store and manage your data, but it will be more expensive.
Ultimately, the decision of which MDM model to use is up to you. Consider your needs and compare them to the different models to find the best fit for your organization.
Implement and Monitor your MDM Solution
Assuming you have already selected and procured an MDM solution, there are still a few more steps to ensure that it is properly implemented and monitored:
- Buy-In from All Stakeholders: To begin, it is important to ensure that there is buy-in from all stakeholders. This includes upper management, IT staff, and, most importantly, employees. If employees do not believe that the MDM solution is necessary or beneficial, they will be less likely to use it correctly, or may find ways to circumvent it entirely.
- Employee Training: Once buy-in has been established, the next step is to thoroughly train all employees on how to use the MDM solution. This training should cover not only the basics of how to use the MDM features, but also common use cases and scenarios. Additionally, it should be made clear to employees that the MDM solution is not optional – anyone who needs to access company data must use it.
- Monitor MDM Solution Usage and Effectiveness: After the MDM solution has been implemented and employees have been trained, it is important to monitor its usage and effectiveness. One way to do this is to set up regular check-ins with employees, either individually or in groups. During these check-ins, employees can be asked about their experience using the MDM solution, any difficulties they have encountered, and any suggestions they have for improvement. Additionally, IT staff should keep an eye on MDM usage statistics, such as the number of devices enrolled, the number of devices accessing corporate data, and the number of devices that are compliant with company policies.
By taking these steps to properly implement and monitor an MDM solution, companies can ensure that their data is properly protected and that their employees are productive.
