What Are MobileConfig and Plist Files?
MobileConfig:
Plist:
How are MobileConfig and Plist files related?
Benefits of using plist profiles
Using plist profiles offers several key benefits for centralized Apple device management, including:
- Simplicity: plist profiles provide an organized and straightforward way to define settings for Apple devices.
- Flexibility: They allow for configuring a wide range of settings, from basic to advanced.
- Automation: They facilitate the consistent application of configurations across all managed devices.
- Cost reduction: They optimize the time and resources dedicated to device management.
- Enhanced security: They enable the application of security policies and restrictions to protect devices and data.
Use cases for plist profiles
Network settings configuration:
Plist profiles allow for the automatic configuration of network parameters, such as Wi-Fi, VPN, and proxy servers. This facilitates secure and efficient connections to corporate networks and other necessary network resources for users.
Security policy implementation:
Application restrictions:
Device format customization:
Application installation:
Considerations for implementing plist profiles
When implementing plist profiles, it is crucial to consider certain aspects to ensure a successful deployment:
- Compatibility: Verify that the plist profiles are compatible with the target device models and iOS/macOS versions.
- Thorough testing: Conduct rigorous testing before deployment in a production environment.
- Effective communication: Inform users about the configuration changes that will be implemented.
- Monitoring and support: Monitor the status of devices and provide support in case of issues.
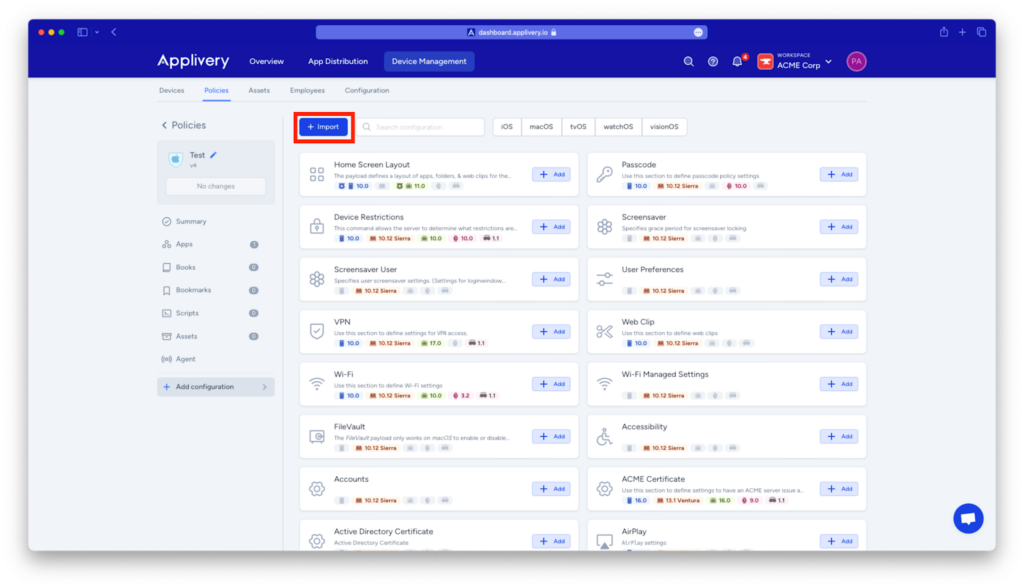
You can deploy customized plist files by uploading MobileConfig files to the policies in your account. Simply access the settings and click the import button to apply the configurations defined in the plist to all managed devices.
With Applivery, you can simplify the deployment and management of these configurations, ensuring that all devices comply with security policies and meet your organization’s specific needs. Take advantage of the automation and customization offered by these tools to optimize your operations and protect your data.