FileVault, available in macOS 10.3 and newer versions, encrypts your entire disk to safeguard your data and prevent unauthorized access on your Mac.
Once enabled, you’ll need a Password or Recovery Key to access your device, ensuring your data remains secure and inaccessible without proper authentication. FileVault also automatically encrypts all new files, providing continuous protection.
Enabling FileVault is a useful configuration to protect your data in case your Mac is lost or damaged.
With Applivery, you have two options for recovery key management (being able to choose how the recovery key is encrypted and recovered):
- Auto (recommended): Applivery will handle the necessary certificates. The recovery key will be displayed in the device settings.
- Manual: You will need to upload the public key. Later, you can download the encrypted recovery key and decrypt it on your device using the private key.
Recovery key management - Auto #
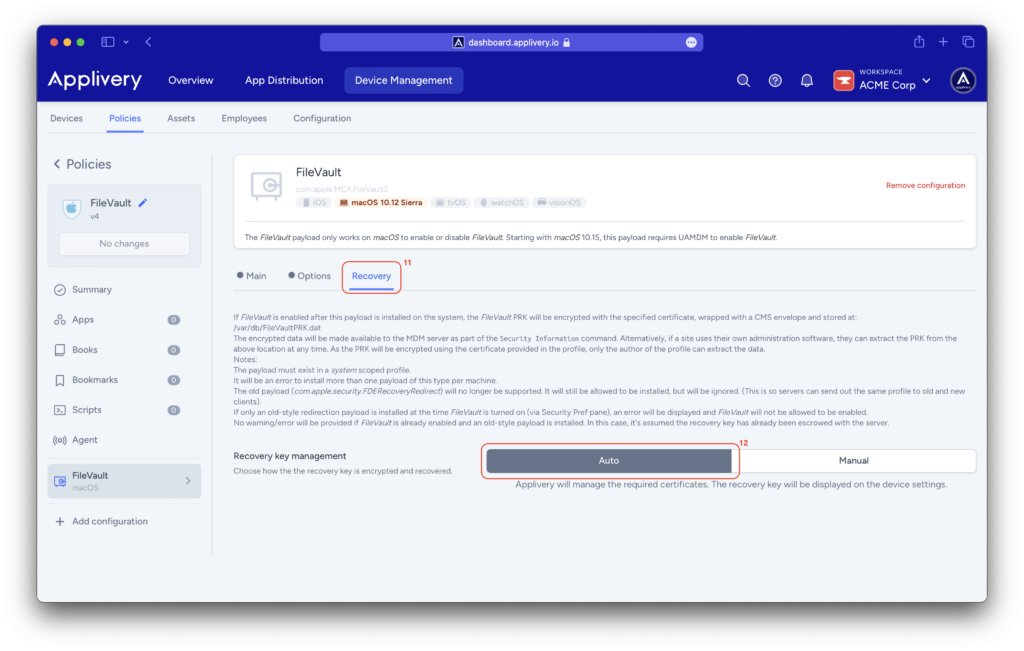
Navigate to your Device Management section, and select Policies (1). Choose the policy where you want to integrate FileVault.
From the left-hand menu, navigate to the + Add configuration (2) option and type FileVault into the search bar (3), then + Add (4) this configuration.
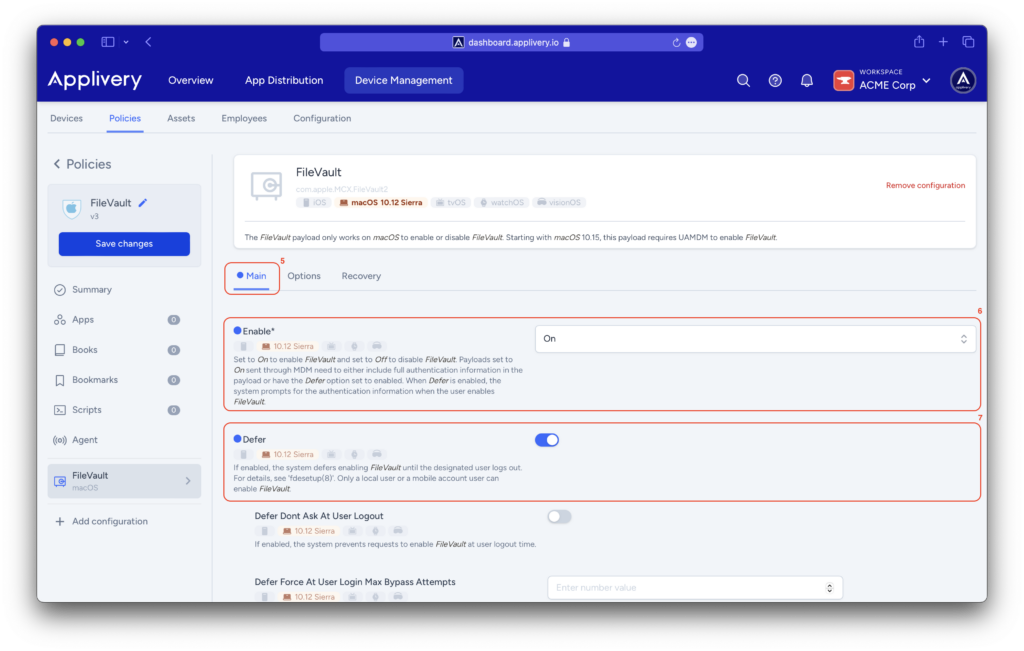
In the Main (5) menu, you will need to Enable (6) FileVault on Mac devices and select the Defer (7) option, which postpones enabling FileVault until the user logs out. Additionally, check the Show Recovery Key (8) option to display it later.
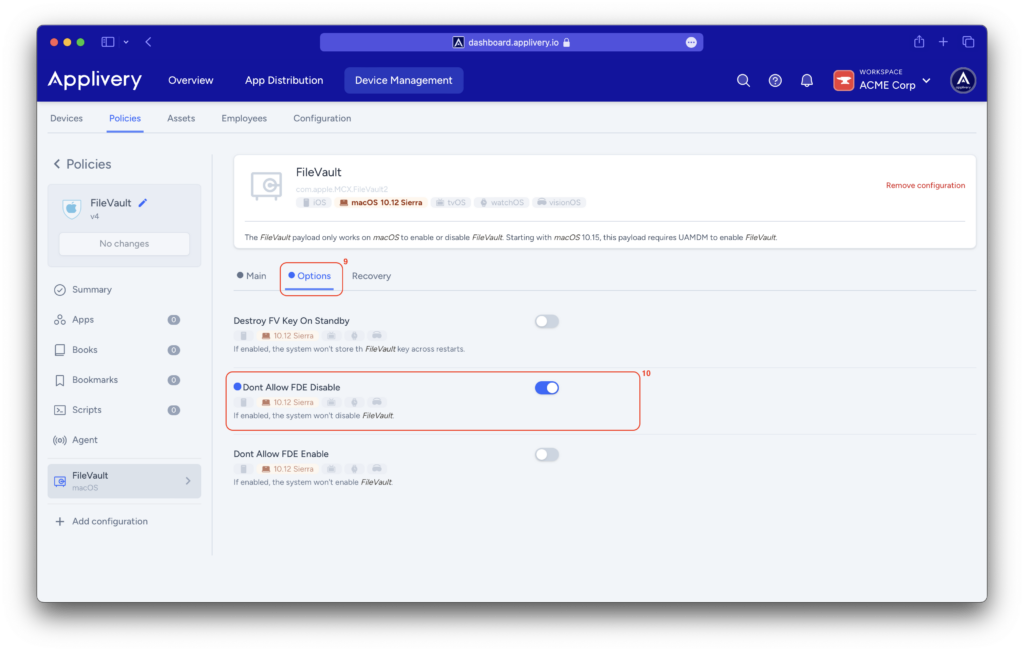
In the Options (9) menu, select Don’t Allow FDE Disable (10) to prevent FileVault from being disabled.
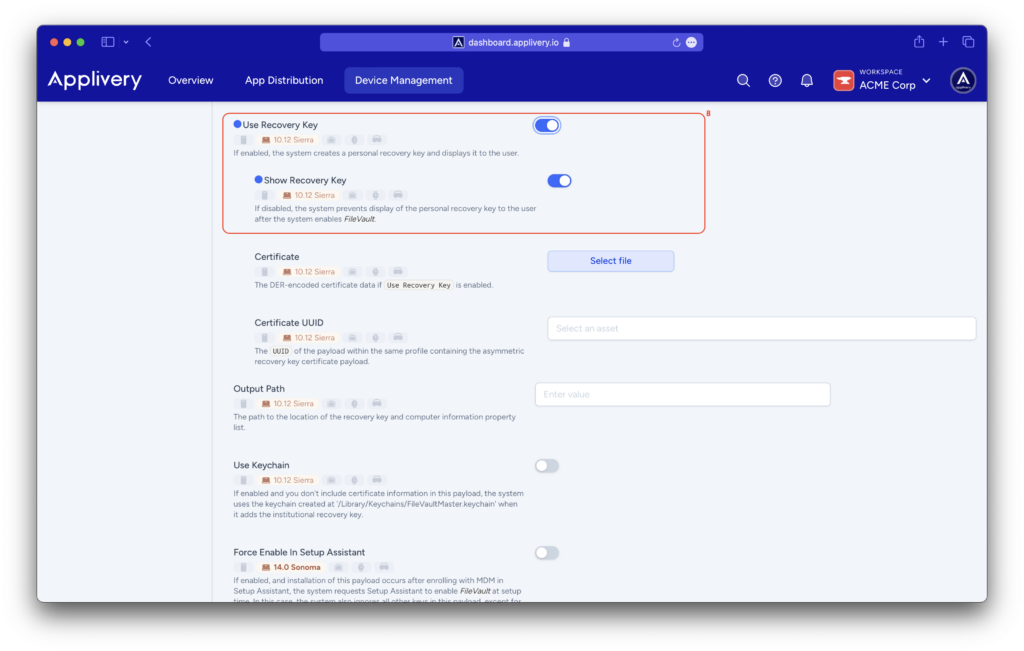
In the Recovery (11) menu, leave the Auto (12) option selected. Applivery will handle the necessary certificates, and the recovery key will be displayed in the device settings.
After saving and updating the policy, the user will need to log out. Upon the next login, the FileVault activation forms will appear.
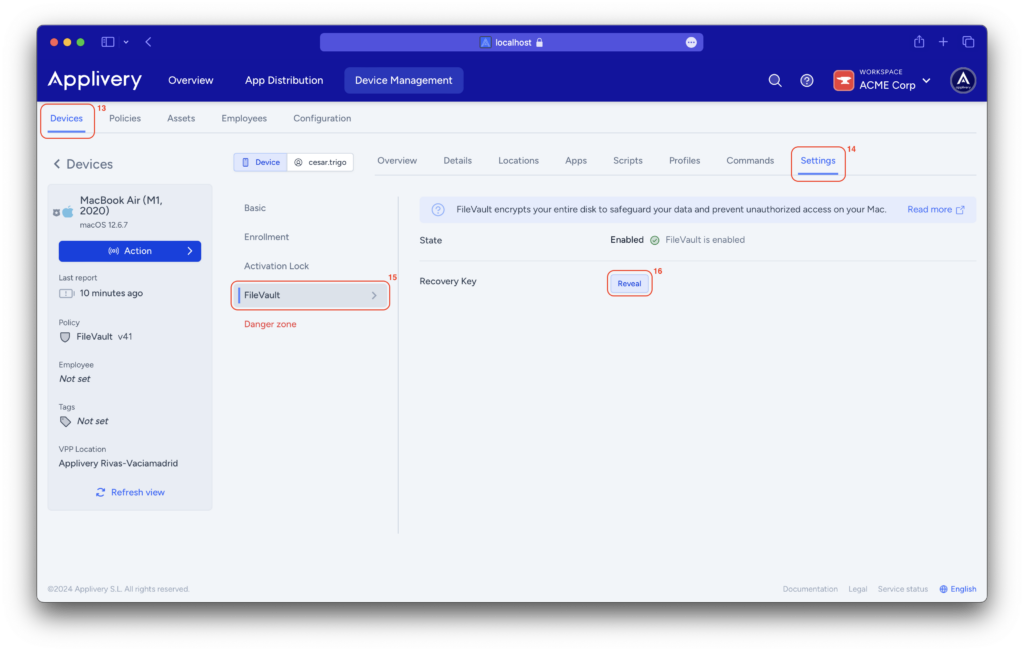
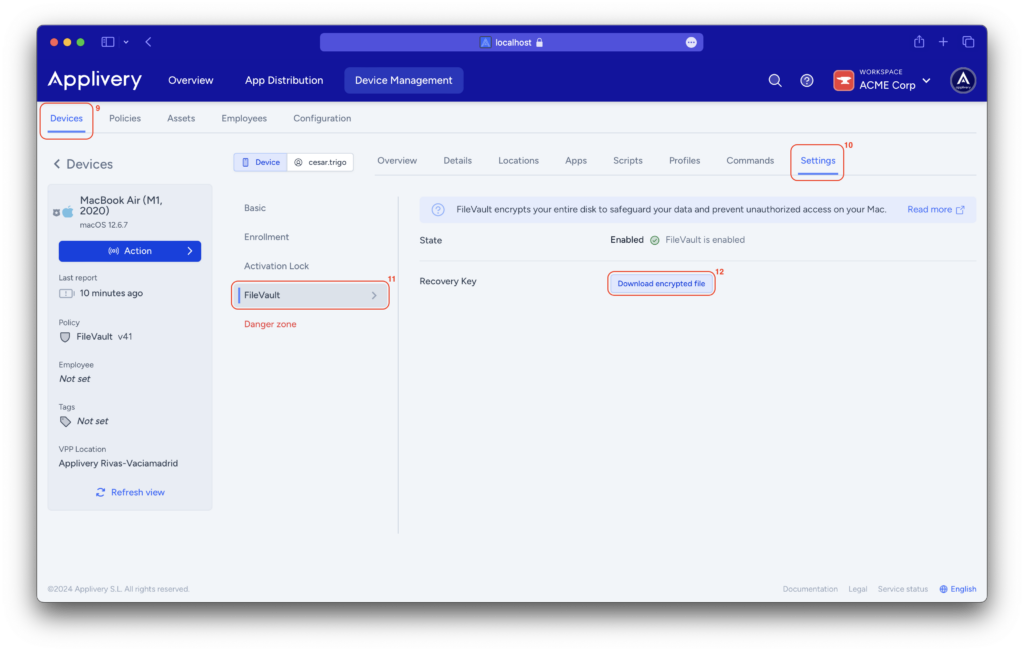
On the Applivery Dashboard, navigate to the Devices (13) section and select the device from which you want to obtain the recovery key.
Go to the Settings (14) > FileVault (15) section and click on the Reveal button (16) to retrieve the recovery key for your device.
Recovery key management - Manual #
Step 1 - Create certificate for FileVault Recovery Key encryption #
To encrypt the Recovery Key, an encryption certificate must be created and uploaded to Applivery.
On a macOS computer (10.8+), open Terminal and execute the command:
openssl req -x509 -nodes -newkey rsa:2048 -keyout private.pem -out public.der -days 365 -outform der
This will generate a public key in .der format.
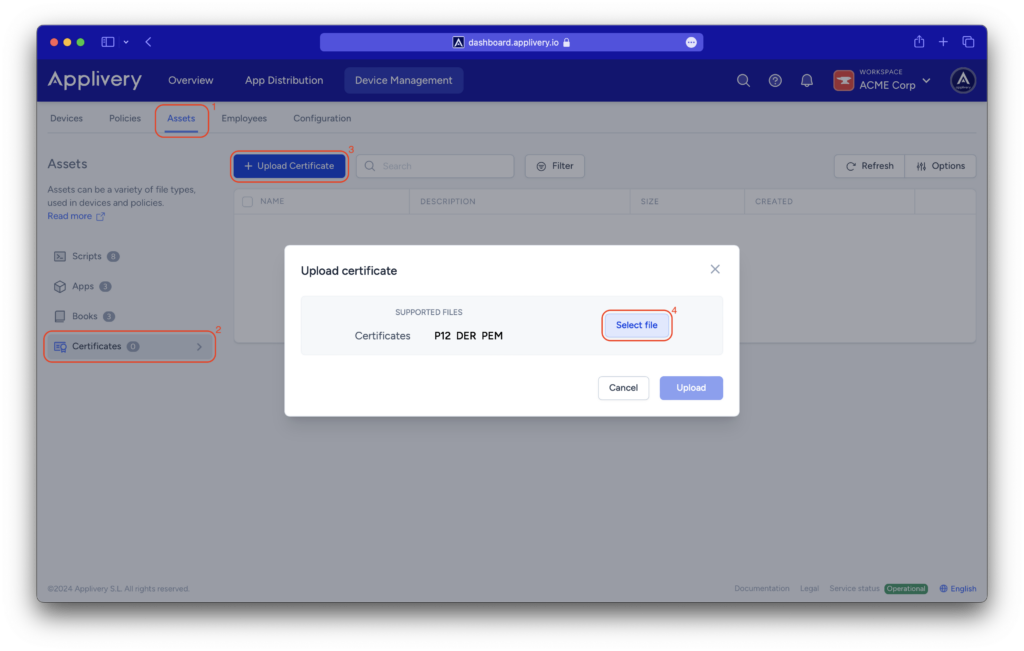
After creating the certificate, go to the Applivery Dashboard and navigate to Device Management > Assets (1), then navigate to the Certificates (2) section and click on + Upload Certificate (3).
A modal view will appear, allowing you to upload the newly created certificate by clicking on the Select file (4) button and loading it from your drive.
Step 2 - Configure policy #
Now, it’s time to begin configuring your FileVault policy.
You will need to perform the same configurations you did in Auto mode for the Main and Options menus. Only the settings for the Recovery menu will be modified.
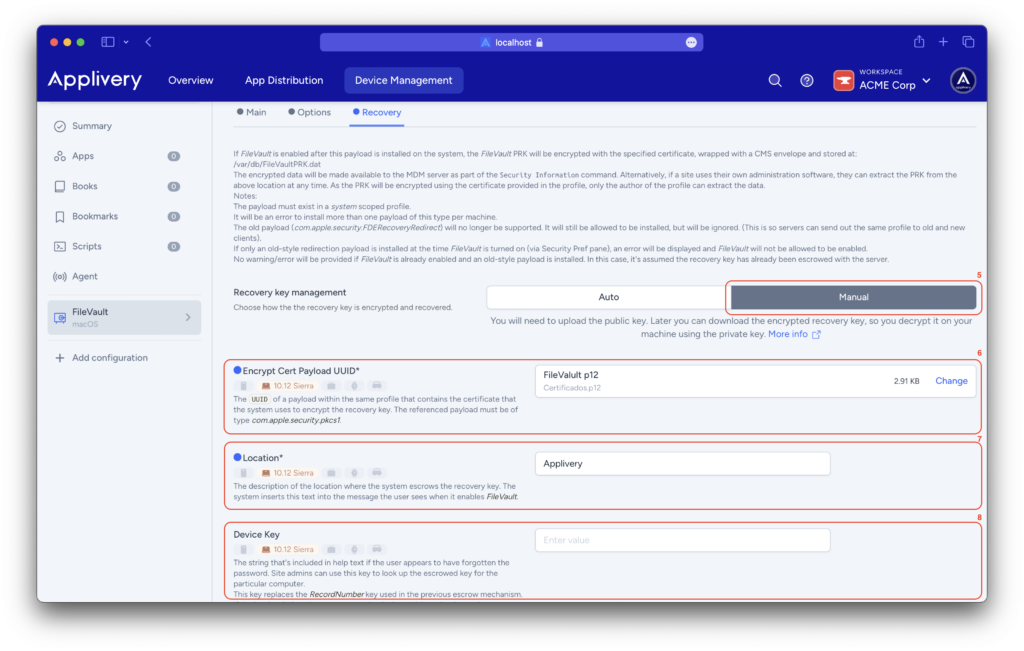
This time, you will select Manual (5) for recovery key management. In the Encrypt Cert Payload UUID (6) field, you will load the certificate previously uploaded in the Certificates section.
Describe the Location (7) field to indicate where the recovery key is stored, ensuring users know where to find it.
For the Device Key (8) field, enter a string (help text) for users who may have forgotten their password. Site admins can use this key to locate the escrowed key for the specific device. This key supersedes the RecordNumber key used in the previous escrow mechanism. If the key is absent, the device serial number is used instead.
Step 3 - What happens at the device end #
After saving and updating the policy on the terminal, the user will need to log out.
Upon the next login, the FileVault activation forms will appear. Once completed, send an Update status command, and you will then have the encrypted key available on the device under the FDE Personal Recovery Key CMS field.
Once the policy is applied, users will not be able to modify the FileVault settings under System Preferences > Security & Privacy > FileVault. The settings as configured in the policy will be enforced.
Step 4 - Retrieving the Recovery Key #
A .dat file will be downloaded and you will need to execute the following command to decrypt the key:
openssl cms -decrypt -in recovery.dat -inform DER -inkey filevault_privateKey.pem